Industrial engineers and operators are the target of a new
campaign that leverages password cracking software to seize control
of Programmable Logic Controllers (PLCs) and co-opt the machines to
a botnet.
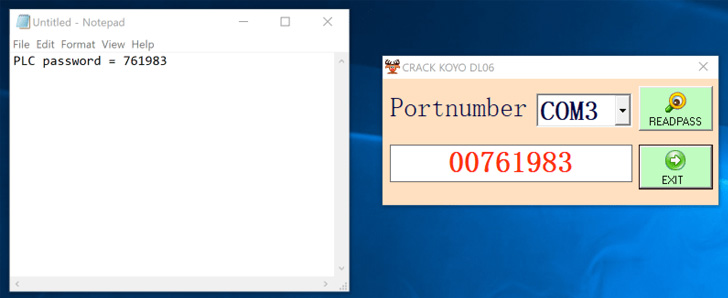
The software “exploited a vulnerability in the firmware which
allowed it to retrieve the password on command,” Dragos security
researcher Sam Hanson said[1]. “Further, the software
was a malware dropper, infecting the machine with the Sality
malware and turning the host into a peer in Sality’s peer-to-peer
botnet.”
The industrial cybersecurity firm said the password retrieval
exploit embedded in the malware dropper is designed to recover the
credential associated with Automation Direct DirectLOGIC 06 PLC[2].
The exploit, tracked as CVE-2022-2003 (CVSS score: 7.7), has
been described as a case of cleartext transmission of sensitive
data that could lead to information disclosure and unauthorized
changes. The issue was addressed[3]
in firmware Version 2.72 released last month.
The infections culminate in the deployment of the Sality[4]
malware for carrying out tasks such as cryptocurrency mining and
password cracking in a distributed fashion, while also taking steps
to remain undetected by terminating security software running in
the compromised workstations.
What’s more, the artifact unearthed by Dragos functions drops a
crypto-clipper payload that steals cryptocurrency during a
transaction by substituting the original wallet address saved in
the clipboard with the attacker’s wallet address.
Automation Direct is not the only vendor impacted as the tool
claim to encompass several PLCs, HMIs, human-machine interface
(HMI[5]), and project files
spanning Omron, Siemens, ABB Codesys, Delta Automation, Fuji
Electric, Mitsubishi Electric, Schneider Electric’s Pro-face, Vigor
PLC, Weintek, Rockwell Automation’s Allen-Bradley, Panasonic,
Fatek, IDEC Corporation, and LG.
This is far from the first time trojanized software has singled
out operational technology (OT) networks. In October 2021, Mandiant
disclosed[6]
how legitimate portable executable binaries are being compromised
by a variety of malware such as Sality, Virut, and Ramnit, among
others.
References
Read more https://thehackernews.com/2022/07/hackers-distributing-password-cracking.html