Apr 07, 2023Ravie Lakshmanan Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to tackle the abuse of Cobalt …
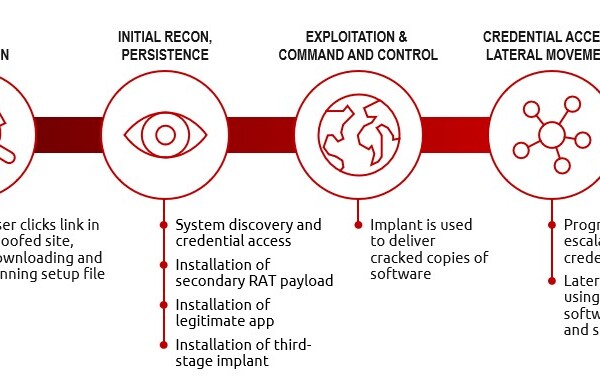


Apr 07, 2023Ravie Lakshmanan Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to tackle the abuse of Cobalt …
Less than a month ago, Twitter indirectly acknowledged that some of its source code had been leaked on the code-sharing platform GitHub by sending a …

Apr 07, 2023Ravie LakshmananIndustrial Control System The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published[1] eight[2] Industrial Control Systems (ICS) advisories warning of critical …

Critical infrastructure attacks are a preferred target for cyber criminals. Here’s why and what’s being done to protect them. What is Critical Infrastructure and Why …

A coordinated international law enforcement operation has dismantled Genesis Market, an illegal online marketplace that specialized in the sale of stolen credentials associated with email, …

A joint international law enforcement operation has dismantled Genesis Market, an illegal online marketplace that specialized in the sale of stolen credentials associated with email, …
Apr 06, 2023Ravie LakshmananPrivacy / Mobile Security Google is enacting a new data deletion policy for Android apps that allow account creation to also offer …

Apr 05, 2023Ravie LakshmananCyber Threat / Malware Portuguese users are being targeted by a new malware codenamed CryptoClippy that’s capable of stealing cryptocurrency as part …
Apr 05, 2023Ravie LakshmananEndpoint Security / Malware An unknown threat actor used a malicious self-extracting archive (SFX[1]) file in an attempt to establish persistent backdoor …

Apr 05, 2023Ravie LakshmananCyber Attack / Cyber Threat A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think …